Key Points:
- SlowMist alerts that opening untrusted project directories in AI coding tools like Cursor can trigger system command execution, compromising developer systems.
- AI tools misinterpret project files like LICENSE.txt and README.md, spreading malware unknowingly across codebases.
- The vulnerability poses serious risks for crypto developers, who store sensitive data like private keys and credentials on their systems.
Blockchain security service provider SlowMist has issued a security warning to developers, warning them to be on the lookout for AI-powered coding tools. The warning is especially directed to those, including Vibe Coding and mainstream Integrated Development Environments (IDEs).
The vulnerability may leave systems to instant dangers, such as the illegal execution of system instructions, endangering the crypto community and assets of the developers with severe threats.
SlowMist’s Finding Could Pose a Threat to Crypto Devs
The burning alert that was issued by SlowMist highlights one of the most significant limitations within the functionality of AI-assisted code rewriters and enables attackers to remotely run system commands by performing simple tasks such as opening a project folder.
The weakness is especially risky as crypto developers keep sensitive information like private keys, wallet data and crypto credentials in their development systems. When developers use untrusted project directories, the vulnerability is triggered, and the user is not required to do other tasks other than clicking the Open Folder button in the IDEs.
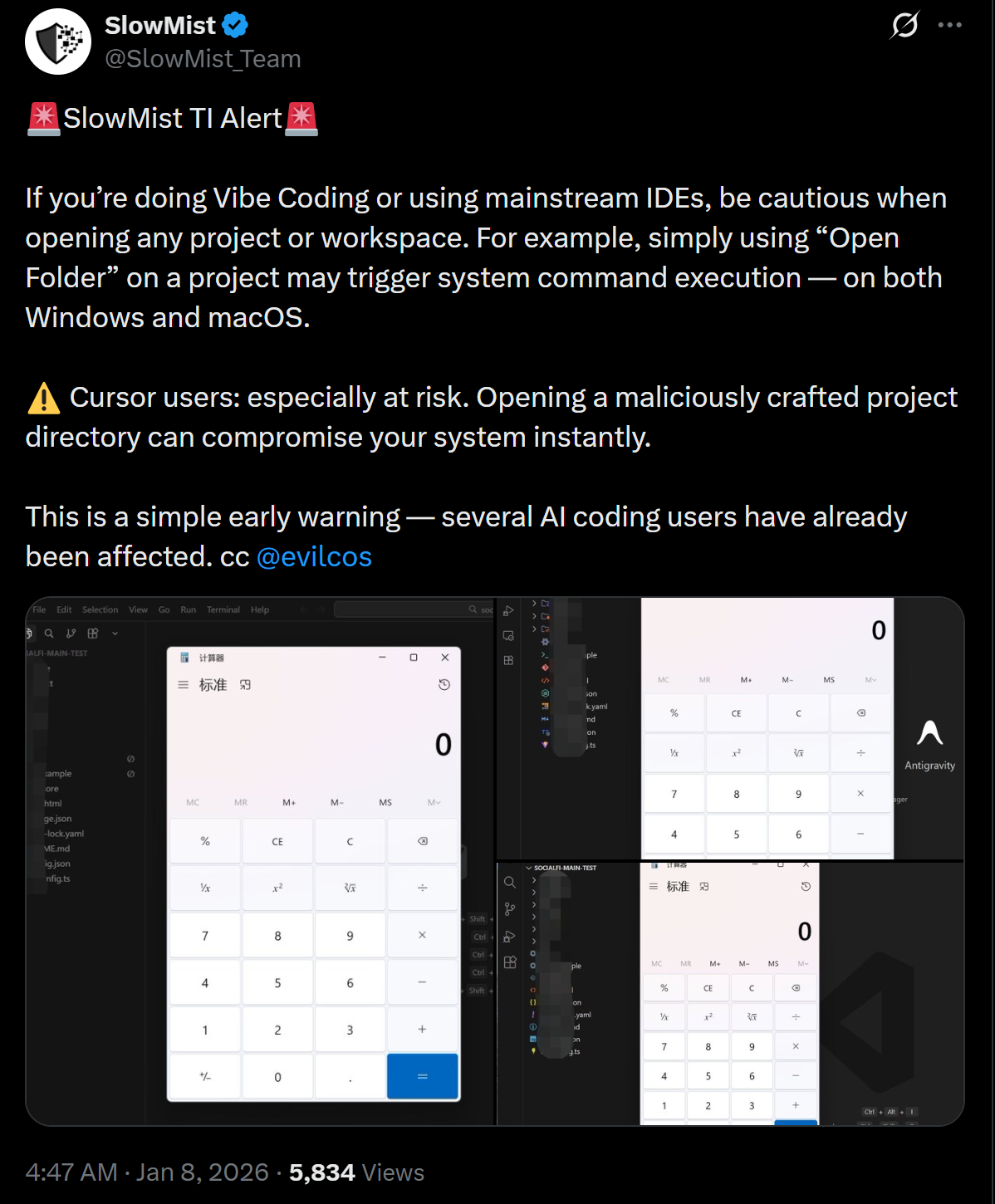
It is a common vulnerability of both Windows and macOS systems, hence a common issue of concern across the development circles. The Cursor IDE is the one that is singled out as the most exploited. The victims of this tool are highly prone to risks, and cases of hacked systems have already been reported.
Malicious Code as an Easy Route to the Top
The weakness is based on an apparently featureless aspect of IDEs, which is opening project directories, unlike other Phishing attacks. System commands are automatically executed as soon as a developer opens a maliciously designed project. SlowMist says that this enables malware to be introduced by the attackers and may steal data, abuse systems, or cause irreparable damage to the environment of a given developer.
The defect has been identified as coming to the Cursor IDE, which is the AI tool of most developers to assist with the code. The weakness is also problematic because it does not need much interactivity on the part of the users.
This type of attack is referred to as CopyPasta License Attack, and it was first observed by a cybersecurity company identified as HiddenLayer in September. It exploits the AI-based tools in understanding and interpreting common project files as the LICENSE.txt or README.md files.
Such files, which apparently are harmless, may contain malicious instructions in the markdown comments. When these files are loaded into the IDE, the malware may be spread through an entire codebase by the AI tools unknowingly and leave entire teams or firms in danger.
This is a vulnerability that can allow attackers to set backdoors or manipulate code or steal sensitive developer data without the knowledge of the victim. The malicious instructions are installed in files in such a manner that they go unnoticed by the developer but can be identified by AI systems that read the files, which activate the attack.
The vulnerability of this nature is highly critical to the industry of cryptocurrency, where such sensitive data as private keys and other credentials is part of the project development. When the attacker accesses the machine of a developer, he/she may possibly steal crypto assets, compromise smart contracts, or even manipulate decentralized applications (dApps).


