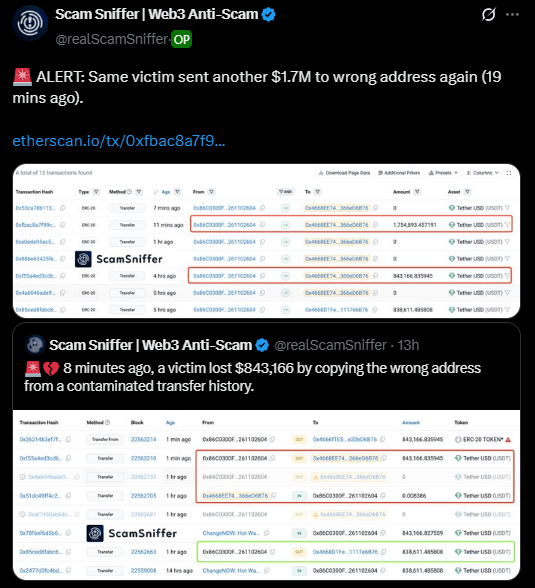
A cryptocurrency user has fallen victim to the same transaction history poisoning scam twice and lost a combined $2.5 million in two separate incidents. According to blockchain security firm Scam Sniffer, the victim first lost $843,166 by copying what they believed was a legitimate address from their contaminated transfer history.
Despite this costly mistake, the same user repeated the error and sent another $1.7 million to a fraudulent address. This shows how effective this particular scam technique has become against even those who have previously been victimized.
Transaction history poisoning has become one of the most insidious crypto scams because it exploits users’ natural tendency to reference their own transaction history when making new transfers. The attack method appears deceptively simple but proves highly effective against unsuspecting victims.
How transaction history poisoning works
The scam operates through a four-step process that takes advantage of users’ trust in their own transaction records. First, scammers send fake or dust transfers using addresses that closely resemble legitimate ones the victim has used before.
These fake transactions subsequently show up in the victim’s history of transfers alongside real transactions. This creates a tainted record. Later on, when customers want to transfer money and are duplicating an address from their history, they are likely to accidentally pick the scammer’s spoofed address instead of the intended recipient.
Finally, the funds end up entirely in the scammer’s wallet instead of where they were supposed to go. This typically equates to irrevocable loss since blockchain transactions cannot be reversed.
SMS phishing attacks are targeted at hardware wallets
Security firm SlowMist uncovered yet another interwoven scam against hardware wallet owners through spoofed SMS messages. Users were receiving SMS messages claiming to be from mainstream exchanges with the following message: “Your withdrawal verification code is xxx. If you didn’t make this transaction, call xxx immediately for assistance.
“When victims dial the number provided, scammers tell them that their security has been breached and they are forwarded to an individual who presents themselves as hardware wallet support. The support operators of the fraud then direct users to phishing sites for stealing mnemonic words.
According to SlowMist, such SMS attack has caused cold wallet thefts of more than $1 million. The attackers leverage users’ faith in well-known exchanges to make the attack seem urgent and real.
Read more: Is Dogecoin Price Ready For $0.3 Breakout?


